The crime of blackmailing iOS devices through Apple ID hacking has become commonplace in recent years, but the recruiters are still in a continuous stream. A few days ago, a friend of his family encountered a real extortion case. The other party directly erased the iPhone that he was using, and asked the owner to pay for the password to unlock the activation lock, and promised to retrieve the erased password. data.
The activation lock (reference link) is an anti-theft feature introduced by Apple from iOS 7. All iOS devices that have logged into the Find My iPhone function will be required to enter the password of the previously logged-in Apple ID account even if the factory default settings or flashing is activated. use. For thieves and robbers, an illegally acquired phone is no different than a tile because it does not know the Apple ID password. This anti-theft feature greatly hit the arrogance of criminals and was highly recommended by the U.S. police (news article). The number of iPhone thefts in San Francisco has fallen by 40%, and New York and London have also fallen by 25%. And 50%, even the FCC has proposed the mobile phone factory trademark anti-theft system (news original).
Returning to the aforementioned friend, although the payment was unlocked but the data could not be recovered eventually, many important photos with relatives were turned into vain. Although I personally think that the friend may be mistaken in the use of the process - such as loss of iCloud backup on weekdays, for example, did not recover the backup data through the correct process - but it is clear that the security of Apple ID can not be ignored.
About Find My iPhone FeaturesAfter this incident, there was a very strange remark in the family circle of friends: Because the phone was locked by the Find My iPhone feature, the Find My iPhone feature should be turned off to prevent the phone from being locked.
The starting point of this kind of speech is really weird. Will someone advise the family not to install electricity because the improper use of electricity may cause personal safety accidents? Turning off Find My iPhone can only reduce the loss of the Apple ID after being stolen and cannot increase the security of the Apple ID. In other words, if the original Apple ID is stolen, the Apple ID may still be stolen after this proposal is implemented . Only guarantee the safety of mobile phones and other devices on it? My own Apple ID has purchased over $1,000 worth of software, and some of the software has already gone offline. Even if you open a new ID, you can't buy it again, let alone other paid media like music, movies, etc. Is the value of ID?
And the deterrence generated by the aforementioned activation locks against criminals is obviously based on the premise that everyone has turned on Find My iPhone for security. Only using Find My iPhone to protect the phone has become a common phenomenon, criminals will be jealous of the power of anti-theft systems and avoid iOS devices such as iPhone crime, all iPhone users can get a more secure use of the environment. If Find My iPhone is turned off by many people, the possibility of profiting after criminals start to increase will increase the incentive for him to commit crimes. What's the use of Find My iPhone alone? The thief will not first investigate whether the machine has activated the lock before deciding whether to start. So for the owners of all iOS devices, the most reasonable choice is to open the Find My iPhone function and protect their Apple ID, so that the account and the device are in a safe environment at the same time. The next article to explain is how to protect the security of Apple ID.
How to protect the security of Apple ID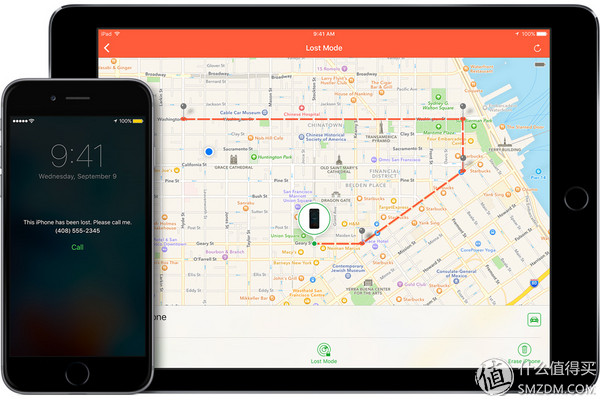
First, set a dedicated strong password for your Apple ID.

Although Apple has a mandatory combination of uppercase and lowercase digital symbols for the user's Apple ID password, Apple cannot know whether the password is used by users on other network services. My personal suggestion is to design a special password combination formula for this most important account to ensure that each network service has a different password. Similar teaching is available on the Internet. Everyone can design their own private password formula. Although I use password management software such as Lastpass and 1Password to manage network passwords, the most important passwords are still written in formulas.
Second, you need to have a secure e-mail address.
The most popular method of hacking nowadays is to use the password of the Apple ID to retrieve the Apple ID by dragging it out of the library login mailbox. Personally, it is recommended to use the e-mail services of mainstream foreign email service providers such as GMail, Outlook.com, Yahoo.com, and Yahoo! Japan , and open the authentication function twice. Ordinary password login uses a (theoretically) password that only you know to verify that you are the owner of the account, but the password may be stolen by someone else. This is where the two verifications come from. In addition to verifying the password, the two verifications also need to verify a specified device to generate/accept dynamic authentication passwords, and your password and designated device fall into the hands of others at the same time. As long as two verifications are opened, even if the attacker has the correct account name and password, he cannot log in. This can protect the information security of the user to the greatest extent.
If you insist on using domestic email, QQ email is almost the only choice, because only QQ email supports an independent password system like two authentications, and it requires a special password to log in to the POP3/IMAP client. If everyone knows which e-mail service provider in the country supports Orthodox verification, please also inform.
Then turn on two-step or two-factor authentication for your Apple ID.
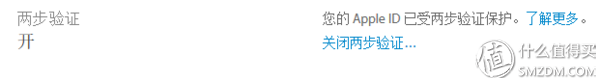
If you don't understand the similarities and differences between two-step verification and two-factor authentication, you can refer to the Minority article: Make your Apple device more secure. Now you should turn on "two-factor authentication."
Finally, add enough powerful security measures to the mobile phone itself.
1. Turn on a sufficient number of lock screen passwords (if you need to use Touch ID you must force open the lock screen password), and enter the wrong password 10 times to erase the phone data.
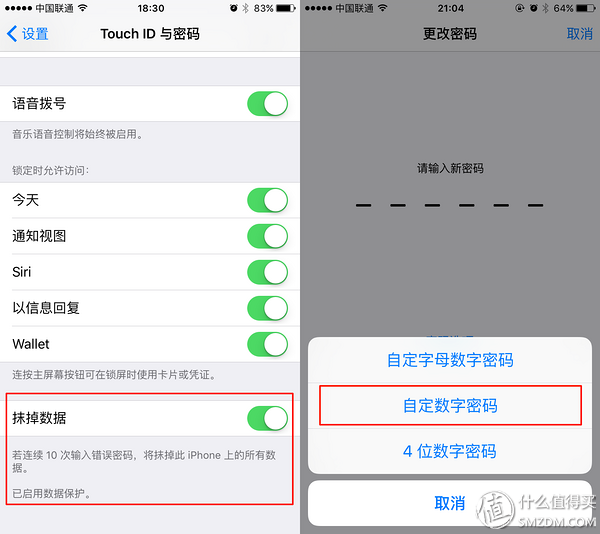
Apple has realized that over-simple lock screen passwords are easily compromised, so the default length of lock screen passwords has been changed from four to six in the latest iOS. I also recommend using a custom total length digital password. This type of password is still much easier to input than a custom alphanumeric password. However, you need to actively click on the “OK†button on the right of the password box to submit it. Peeping and guessing difficulty. As far as entering 10 incorrect passwords, automatically erasing the phone's settings will make it even harder for the FBI to compromise, let alone an ordinary thief.
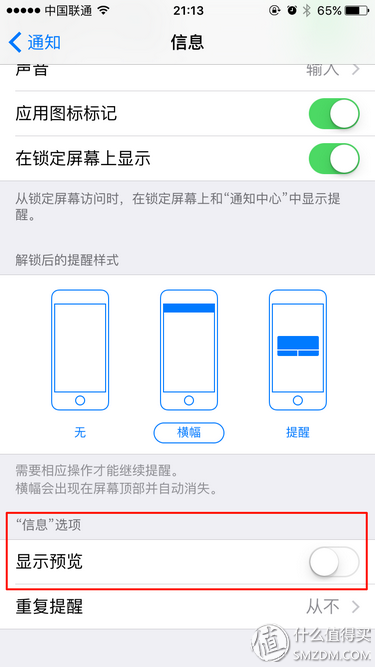
2. The phone text message cannot be previewed on the lock screen. This setting protects the SMS verification code from being directly viewed on the lock screen, not only for the Apple ID, but also for all services that use the SMS verification code.
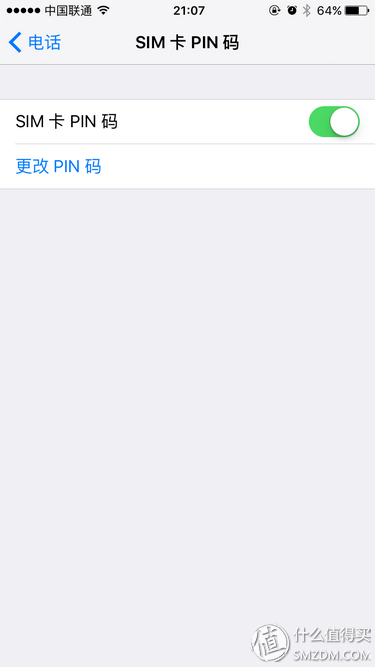
3. Turn on the custom SIM card PIN code. This is a protection measure for the phone number itself. You need to enter the SIM card PIN code to use the phone after you restart the phone or take the SIM card to another phone. If you enter the wrong number three times, the SIM card will be locked permanently. It does not shut itself down and the lock screen password is compromised, or even the owner's own phone number will not leak. All SIM cards have their PIN code function disabled by default. After entering the default PIN code on the SIM card, the new PIN code can be reset. Please consult your own operator for the preset value.
Well, let's simulate the various possible information leakage scenarios and demonstrate whether such settings are safe enough.
Apple ID password leakIn fact, regardless of whether Apple ID's two-step authentication or two-factor authentication is turned on, the leakage of the Apple ID password is not a problem. Naturally, there is no need to say two-step authentication or two-factor authentication. The hackers cannot even access the account management page. Even if there is no two-step authentication or two-factor authentication and they can directly log in to the account management page, they need to enter the security question to be able to change the password. Relatively speaking, there is no great risk. However, even if two-step verification/two-factor authentication is turned on, hackers can directly access icloud.com to lock or directly erase the device to which the Apple ID is bound. This should be because Apple considers that the user cannot verify the lost phone. Lock the design of lost devices as soon as possible. Although locked mobile phones can be instantly unlocked and erased through a lock screen password, all mobile phones can also be restored through iCloud backup. However, this is a very troublesome result, so designing a secure Apple ID password helps to avoid the above troubles. .
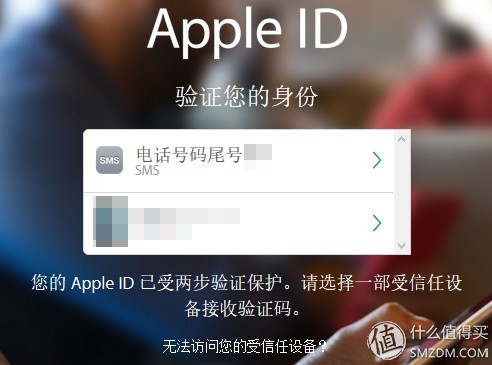
In addition, Find My Mac's rules are different from that of Find My iPhone. The usual advice is not to open Find My Mac. This is another topic.
Apple ID email password leakThis shows the need for two-step verification/two-factor authentication. If you do not enable such security features, hackers can directly reset the Apple ID password through the password recovery process on the official website, and then modify the Apple ID's email address to their own to fully own the Apple ID. This is to use.哔哔 E-mail is the reason why users of Apple ID are frequently hacked.
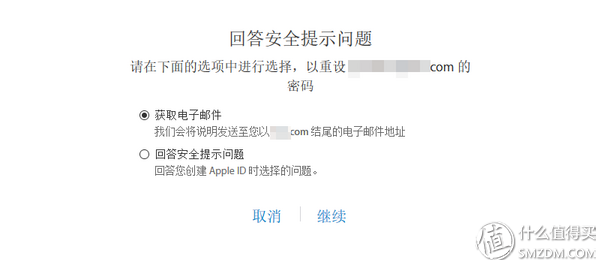
 If the Apple ID has two open verifications, the recovery password will be required to enter the recovery key that was generated at that time. If there is no recovery key, the password cannot be recovered. If the user properly stores the recovery key in a physical form at home, the chance for the hacking person to obtain the key is minimal.
If the Apple ID has two open verifications, the recovery password will be required to enter the recovery key that was generated at that time. If there is no recovery key, the password cannot be recovered. If the user properly stores the recovery key in a physical form at home, the chance for the hacking person to obtain the key is minimal.
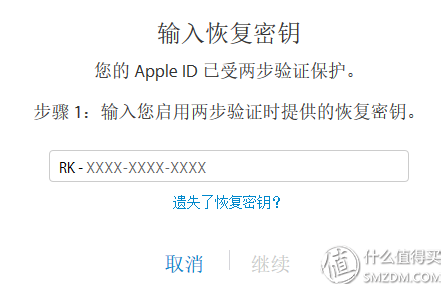
In the case of two-factor authentication, the first step in retrieving a password is to verify the phone number. Although it is not as secure as a two-step authentication key, it is safe enough.
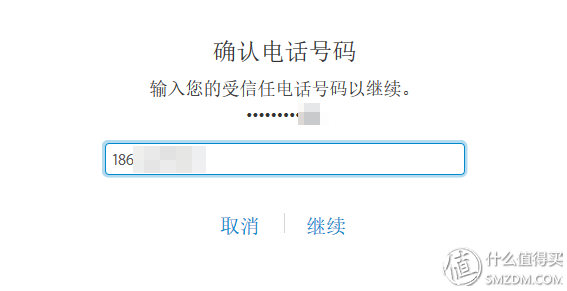
A mobile phone that can work can receive emails from Apple ID emails and can receive SMS verification codes. The security of the owner's information will be in a very dangerous situation. Of course, if the lock screen password is not compromised, thieves and hackers can only do nothing but obtain the email address to which the Apple ID belongs. This situation is not worth assuming.
With 2-Step Verification turned on, modifying the iCloud settings or entering Find My iPhone requires re-entering the Apple ID password. Even if the phone can access Apple ID's email address, the iCloud password cannot be modified. This is safe for IDs. Only thieves and hackers will have the opportunity to use Apple Pay and peek through other data that requires Touch ID authentication by entering their fingerprints. If a mobile phone with a weak lock screen password is lost, be sure to erase it promptly through Find My iPhone. Its data - this time again shows the importance of Find My iPhone.
In the case of enabling dual authentication, it is a bit subtle. Just enter the lock screen password again to modify the Apple ID password from the mobile device so that you have full control over the Apple ID. Then go to the web page to modify the Apple ID email address. The owner will completely lose ownership of the account. At the same time, mobile My Find iPhone can log in and lock other devices without entering any password. Moreover, since the local lock screen password has been cracked, it can be modified. At this time, the original owner will not be able to restore the control of other locked devices.
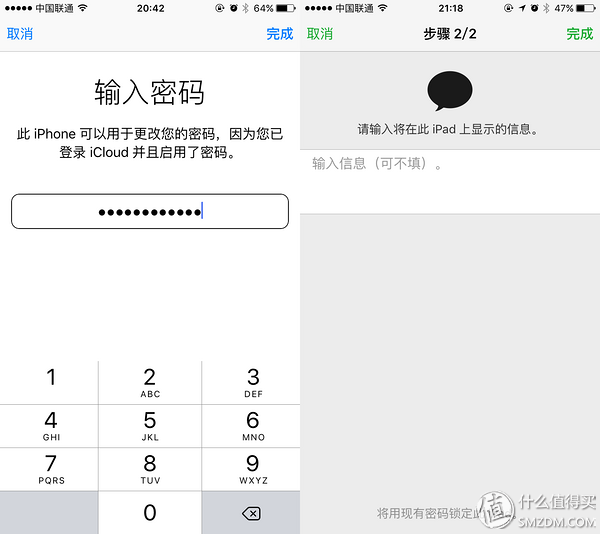
In this case, thieves and hackers will be able to easily take full control of the Apple ID and the devices bound to this Apple ID, or even go completely away from the password recovery process of the e-mail, so you can easily modify the phone as long as you have a mobile phone. password.
So I think that two-factor authentication is more fragile than two-step verification . With two-factor authentication enabled, a device with an Apple ID login plus a valid lock screen password will have full permissions for this Apple ID. Although the two-step verification is more troublesome than the two-factor authentication, the security is flawless. Of course, double authentication is safe enough if you think your phone lock password is strong enough to be compromised.
But I still think that two-step verification is a better choice, because it is not inferior to two-factor authentication in the scenario that I can imagine, and even better. The only key to the two-step verification is to have a secure laptop to record the recovery key, so I'm afraid that the dual authentication is more suitable for some users who do not have a stable residence. After all, when you need to find the verification code, you can't find a small notebook to be completely lost. Now. On the other hand, Apple ID's password is almost impossible to be modified by the hackers after it turns on two-step authentication. However, in the daily behavior of using Apple ID, it is often required to enter this password, so the possibility of forgetting is also minimal. There is no need to use a recovery key to retrieve the password.
So the key to protecting the Apple ID and its bound devices is to set up dual or two-step authentication, add a strong lock screen password to your device, and open Find My iPhone to lock or erase your phone in time. To protect your personal information . It is hoped that each Apple device user can use his own account reasonably to maintain his own rights and the safety of the entire ecosystem.