After the products are shipped from the factory, the chips are often encrypted by software and hardware. If the products need to be cracked, the decryption of the encrypted chips generally requires dismantling the chips and analyzing the internal bus structure. The cracking period is long and expensive. But many times code is often leaked during production. This article will show you how to prevent code leaks during production.
There are many companies that choose the foundry to mass-produce after the product development is completed. The security of the code is especially important. In order to avoid the factory direct contact with the code, the encryption project is generally established on the programmer, the burned file is encrypted and protected, and then the encrypted project is sent to the foundry to prevent the file from being directly leaked.
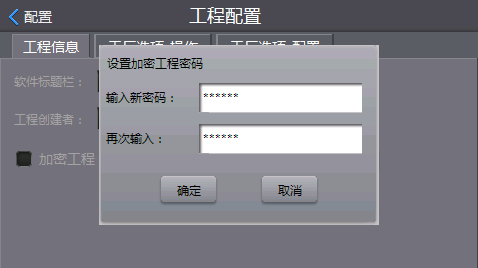
Figure 1 Engineering Encryption
The traditional burning method is erasure-programming-checking-encryption. This method can ensure that the chip is in an encrypted state after the burning is completed, which eliminates the possibility of code leakage to a certain extent, but it is not invulnerable, as long as a small action It is easy to steal the code inside the chip. For example, after the burn is performed, the erase (write) is performed, and the board (chip) is disconnected from the programmer's connection during the verification, so that the burn is not performed until the encryption phase. At this point, the chip is in a state of being burned but not encrypted, and a programmer can read its internal code, causing code leakage.
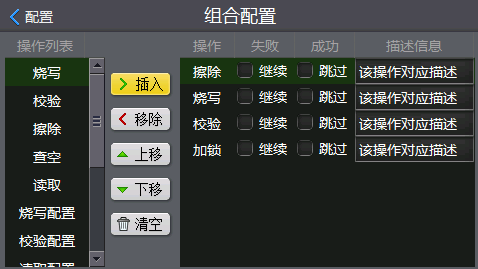
Figure 2 Traditional burning method
In order to solve this problem, the P800isp programmer provides a combination of flexible editing configurations, the operations in the combination can be arbitrarily increased or decreased, and the execution order can be adjusted. In order to avoid code leakage during production, the combination sequence can be adjusted to erase-encryption-programming-checking, which is encrypted before programming. This ensures that once the chip is reset (or powered down), the encryption will take effect after the programming is completed. , reading internal code is prohibited. Of course, this method also needs the support of the chip itself. Some chips will take effect immediately after performing encryption, such as MicroChip's PIC series chip, ATMEL's ATSAM4C series chip, etc., which can only use the traditional burning mode.
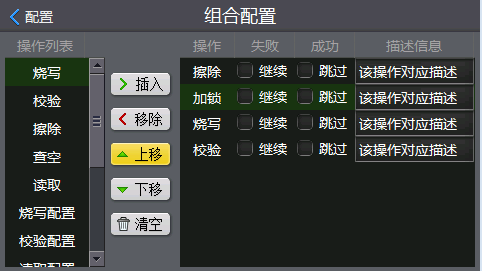
Figure 3 Custom security encryption
Laptops,windows Laptops,win11 Laptops,win10 Laptops
Jingjiang Gisen Technology Co.,Ltd , https://www.gisentech.com