The reader conflict is the interference detected by one reader and caused by another reader. It mainly has three manifestations.
(1) Interference between the reader and the reader: When a strong signal transmitted by a reader interferes with a weak signal reflected by a RF tag, it causes a gap between the reader and the reader. The interference is shown in Figure 1. The reader R1 is located in the interference area of ​​the reader R2. The signal reflected back from the RF tag T1 reaches the reader R1 and is easily interfered by the signal transmitted by the reader R2. This kind of interference is possible even if the reading range of the two readers does not overlap.
(2) Interference from multiple readers to tags: When multiple readers read the same tag at the same time, it causes interference between multiple readers and tags. As shown in Figure 2, the reading range of two readers overlapping. The signals transmitted from the readers R1 and R2 may cause interference at the radio frequency tag T1. In this case, the tag T1 cannot decrypt any inquiry signals and neither the readers R1 nor R2 can read T1. Because the reader conflicts, the reader R1 can read the tags T2 and T3, but cannot read the tag T1. Therefore, the reader R1 indicates that two RF tags exist instead of three.
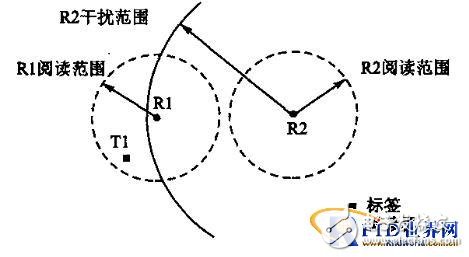
Figure 1 Interference between the reader and the reader
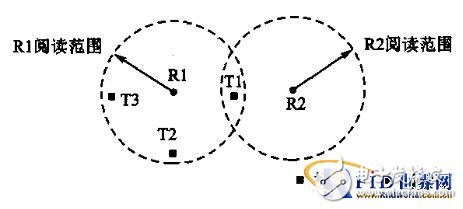
Figure 2 Interference from reader to tag
(3) Reader conflicts invalidate carrier sense: Another case where readers collide is shown in Figure 3. The read range of the two readers does not overlap, but the signal transmitted by the reader R2 and the signal transmitted by the reader R1 interfere at the tag T. This situation occurs simultaneously when the two readers are not in the mutual listening range, which invalidates the carrier sense in the radio frequency identification network.
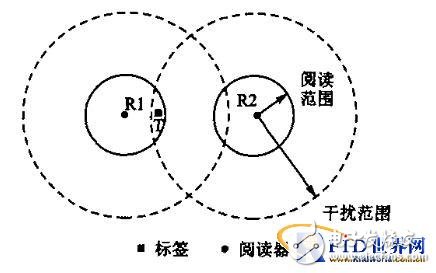
Figure 3 Reader conflicts invalidate carrier sense
In addition to misuse, reader conflicts also slow down the overall reading rate of the RFID system, and these problems are exacerbated in mobile or handheld readers. Therefore, it is necessary to reduce the reader conflict.
2 Related work and research2.1 Main features of reader conflict
The reader conflict has the following characteristics:
1 Hidden node problem is an aspect of the reader conflict problem. When two readers are not in the mutual listening range and interfere at the tag, normal carrier sensing in the radio frequency identification network cannot work.
2 When multiple readers interrogate/transmit signals at a radio frequency tag, the signal at that point becomes very messy and the RF tag can no longer receive any reader interrogated/transmitted signals.
The RF tags studied were passive tags, so the tags themselves could neither be adjusted nor actively communicated with the reader to avoid conflicts. The radio frequency tag can be communicated after being activated by the interrogator signal.
2.2 Related multiple access mechanisms
Commonly used multiple access mechanisms cannot be directly applied to RFID systems because:
1FDMA. In the FDMA mode, the reader uses different frequencies to communicate with the RF tag. Since the RF tag does not have a frequency tuning circuit, the RF tag cannot select a particular reader to communicate with it. If the RF tag adds a frequency tuning circuit function, the cost of the RF tag will be greatly increased, so FDMA is not suitable for use in the RFID system.
2TDMA. In the TDMA mode, the readers are assigned different time slots to prevent the reader from simultaneously interrogating/transmitting RF signals. This is similar to the graphics coloring problem in graph theory and is an NP-hard problem. In a mobile network, the interfering readers do not interfere because of the proximity of the mobile, and the time slots need to be reassigned. Dynamic allocation of time slots reduces the reading rate of the RFID system.
3CSMA. RFID networks, like other wireless networks, have hidden node problems. The reader does not interfere at the tag within the mutual listening range, so relying solely on carrier sensing cannot avoid conflicts in the RFID network.
4CDMA. CDMA requires additional circuitry on the RF tag, which greatly increases the cost of the tag, and assigning codes to tags in all networks is a very complicated task. Therefore CDMA is not a low cost and effective solution.
2.3 Related anti-collision mechanisms
Common anti-collision protocols, such as RTS-CTS, cannot be directly applied to RFID systems because:
1 In a traditional wireless network, only one node sends back a CTS signal to the sender. However, in the RFID system, if the reader broadcasts an RTS signal, all tags in the reader's reading range must send a CTS signal back to the sender's reader. This requires the design of additional anti-collision mechanisms for these CTS signals, which will make this protocol more complicated.
2 It is possible that some tags (such as T1) did not receive the RTS signal and others (such as T2) received the RTS signal due to the conflict. In this case, the CTS signal sent back from T2 cannot be determined to have no conflict within the reading range of the reader. How to determine the CTS signal that the reader has received all the tags in its reading range is very important for the reader to have conflicts.
2.4 Related reader anti-collision methods
Curing Screen Protector,Hydrogel Phone Cutting Machine,Protective Film Cutter Machine,Screen Protcter Custting Machine
Shenzhen TUOLI Electronic Technology Co., Ltd. , https://www.hydrogelprotectors.com