At present, targeted attacks have become one of the main attacks that threaten enterprise security. They are often hidden under the large number of alerts generated by security systems, giving attackers time to invade enterprise systems and steal valuable data.
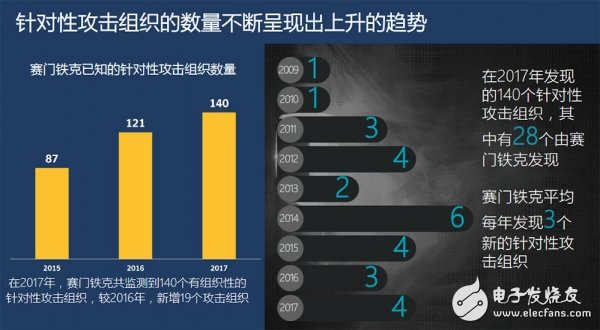
With the constant evolution of the security situation, targeted attacks have begun to change. According to Symantec's statistical report, the number of targeted attack organizations is increasing year by year. Currently, 140 targeted attack organizations have been discovered, an increase of 19 from 2016.
Target and motivation for targeted attacks
For targeted attacks, the attacker no longer attacks a wide range of consumers, individual users, or general enterprises, but only attacks against a certain enterprise. This hacker organization is called a targeted attack organization.
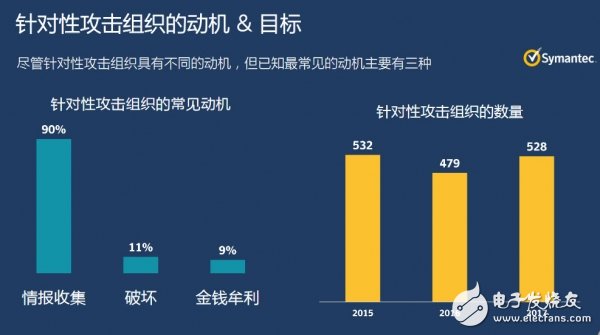
The first attack process of targeted attack organizations, the first is intelligence gathering. Most of the work of hacker organizations is actually to collect intelligence first. Then, they will choose to do destructive actions against the enterprise. The ultimate goal is to obtain money and profit. These are the main motivations and goals for targeted attacks.
Main attack
The most common method of targeted attacks is phishing, which is closely related to people's work and lifestyle. For example, when our mobile phone receives mail, we can only see the name of the mail, but we can't see the domain name of the mail, which is often used by hackers. Because mail is the most common application for business employees when using portable devices and smart terminals, it also has access to corporate-related data. Therefore, hackers can easily exploit these vulnerabilities to attack enterprise data. The use of a large number of mobile devices and the relaxation of employee vigilance are also one of the important reasons for the high success rate of phishing.
The second common method is called puddle attack. If a hacker organization wants to attack a target company, then he will first understand what type of website the employees of the target company usually visit, and even the websites of their upstream and downstream suppliers. The ideas and goals of hacker organizations are very simple. They choose websites that are trusted or frequently visited by enterprises, especially those that allow employees to visit. Once hackers cannot directly attack the main website of the target enterprise, they will frequently visit the employees of the enterprise. Other sites serve as a breakthrough for attacks.
According to statistics, the combination of phishing and puddle attacks accounted for 95% of the total targeted attacks. However, when hackers try to attack, they often use a method that uses multiple methods to launch attacks. Therefore, the safety awareness of employees is very important to the company, and the company should train employees' safety awareness in a timely manner.
How to prevent attacks
Nowadays, many enterprises use a lot of sandbox products and technologies in the prevention of such attacks or unknown dangers, as well as products such as abnormal detection. This leads to a huge task for users, and a large number of analysis and testing work needs to be completed by the enterprise itself. . This has been stretched for the increasingly frequent and complex attacks. In this regard, Wang Jingpu, technical manager of Symantec's East China and South China region, said that these tasks can be completely moved to the cloud to complete, and then the results are returned to the enterprise after the completion of the process, which is also Symantec's Advanced Threat Defense (ATP) The original intention of the solution.
Wang Jingpu, Technical Manager, East China and South China, Symantec Corporation
In addition, Wang Jingpu said that in the past, it was often isolated to scan a file for problems, or to look at network traffic at a certain point in time or within a certain period of time. This is called a separate scan. But Symantec's detection and scanning involves all the activities within the enterprise, that is, the activities on the terminal and the traffic on the network can be analyzed. Our analytical tools are placed in the cloud while using artificial intelligence and some models of machine learning for analysis.
Algorithm and sample are indispensable
At present, many companies are doing research and development related to machine learning and artificial intelligence. Wang Jingpu believes that if the input sample is not typical and the sample coverage is not wide enough and not large enough, then the machine-learned model may not be the model that best matches the business, and the output result must not be the best. Therefore, both the algorithm and the sample of the input data are critical and indispensable. The algorithm is good, but there is no sample, no typical data, the data output will not be good. Of course, even if there is a huge amount of data and there is no good algorithm, it may take many years to calculate it, which is unrealistic.
The advantage of incorporating artificial intelligence lies in the large sample of analysis that can be built using hundreds of millions of control points and a large customer base around the world. This is a big breakthrough compared to single customer analysis, so the analysis results will be more accurate.
In the analysis process, we first need to collect data. In terms of breadth, Symantec has protected 175 million terminals worldwide, with 80 million proxy endpoints. For endpoint traffic and email, there are 95 million worldwide. Sensors, as well as bait mailboxes, allow for the collection of a wide range of data worldwide. In addition to the collected data, processes and system events on the endpoints in the enterprise are also collected. Coupled with different industries, different customers, different types of equipment, machines, and data sources formed through these.
Wang Jingpu said that when collecting events, first, we will not affect the user's terminal; second, it will not cause it to conflict with any other software or system on the endpoint; third, we will ensure anonymity. It does not involve the collection of information related to corporate secrets. We have also made some changes to the analysis engine of the cloud core endpoints to achieve a balance that ensures both the performance of the user's system and the privacy.
Security protection depends on the cloud
Wang Jingpu stressed that the protection of targeted cyber attacks in the future will mainly depend on the cloud. According to predictions, not only will we use artificial intelligence, machine learning and other technologies in the future. Similarly, hackers use artificial intelligence and advanced machine learning to launch attacks, thus forming a competition mode. Then, whether we can keep up with the hacker's attack pace with the pace of machine learning and artificial intelligence becomes the key.
For security vendors, the scope of future monitoring, the amount of data, and the response time of the analytics engine will be their main core competencies. Currently, Symantec has moved the entire system from its own data center to the cloud and launched targeted attack analysis (TAA) technology in advanced threat prevention (ATP) solutions to help enterprise users respond to the corresponding threats. This is because only the combination of the huge computing power of cloud computing and the big data analytics platform can better cope with the complex threats of targeted attacks in the future.
Manual Hydraulic Valve Remote Control Device
The manual valve remote control device consists of a fixed manual hydraulic pump, a hydraulic driver and a butterfly valve. The device takes a single valve as the remote control operation object, and has the characteristics of compact structure, simple operation, convenient operation and maintenance, etc. It is suitable for remote opening and closing control of special position valves in oil tankers, chemical tankers, oil platforms and other ships.
marine Controls device,Manual hydraulic valve remote control device size,black marine controls device
Taizhou Jiabo Instrument Technology Co., Ltd. , https://www.taizhoujbcbyq.com